Understanding AWS Resource Control Policies (RCPs): A Comprehensive Guide
Managing permissions and access control effectively is crucial for organizations. AWS Resource Control Policies (RCPs) emerge as a powerful tool in this domain, offering centralized control over resource permissions within your AWS organization.
What are Resource Control Policies?
RCPs serve as guardrails for your AWS organization, helping ensure that resources across your accounts maintain compliance with your organization’s access control guidelines. These policies don’t grant permissions directly but instead set the maximum permissible actions on resources.
Important Characteristics of RCPs
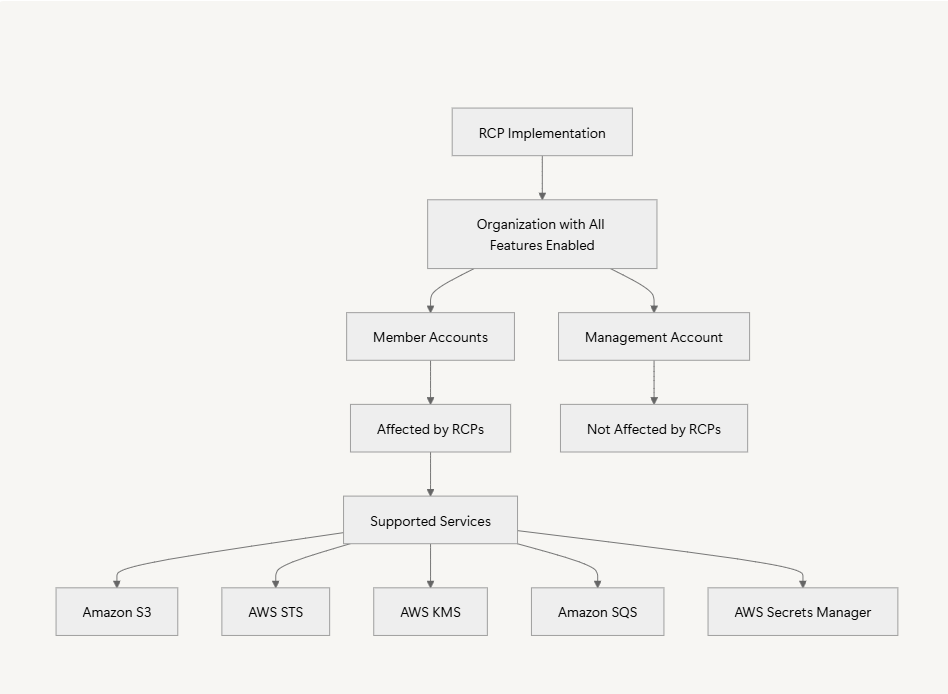
- ✅ Only available in organizations with all features enabled
- ✅ Affects member accounts only, not the management account
- ✅ Applies to specific AWS services (S3, STS, KMS, SQS, Secrets Manager)
- ✅ Works alongside existing IAM policies
Best Practices for Implementation
- Testing Strategy
- Start with individual test accounts
- Move to lower-level OUs
- Gradually work up the organization hierarchy
- Monitor CloudTrail logs for Access Denied errors
Limitations and Exceptions
- ❌ Cannot restrict actions in management account
- ❌ Does not affect service-linked roles
- ❌ No impact on AWS managed KMS keys
Lets get Started:
To enable RCPs, you can use the Organizations console, an AWS SDK, or the AWS Command Line Interface (AWS CLI). Note that only the Organizations management account or a delegated administrator can enable or disable policy types.
Before proceeding, ensure you’re using Organizations with the all features option enabled. If you’re currently using Consolidated billing features , you’ll need to migrate to all features first.
For console users, navigate to the Organizations console, select Policies, and look for the option to enable Resource control policies.
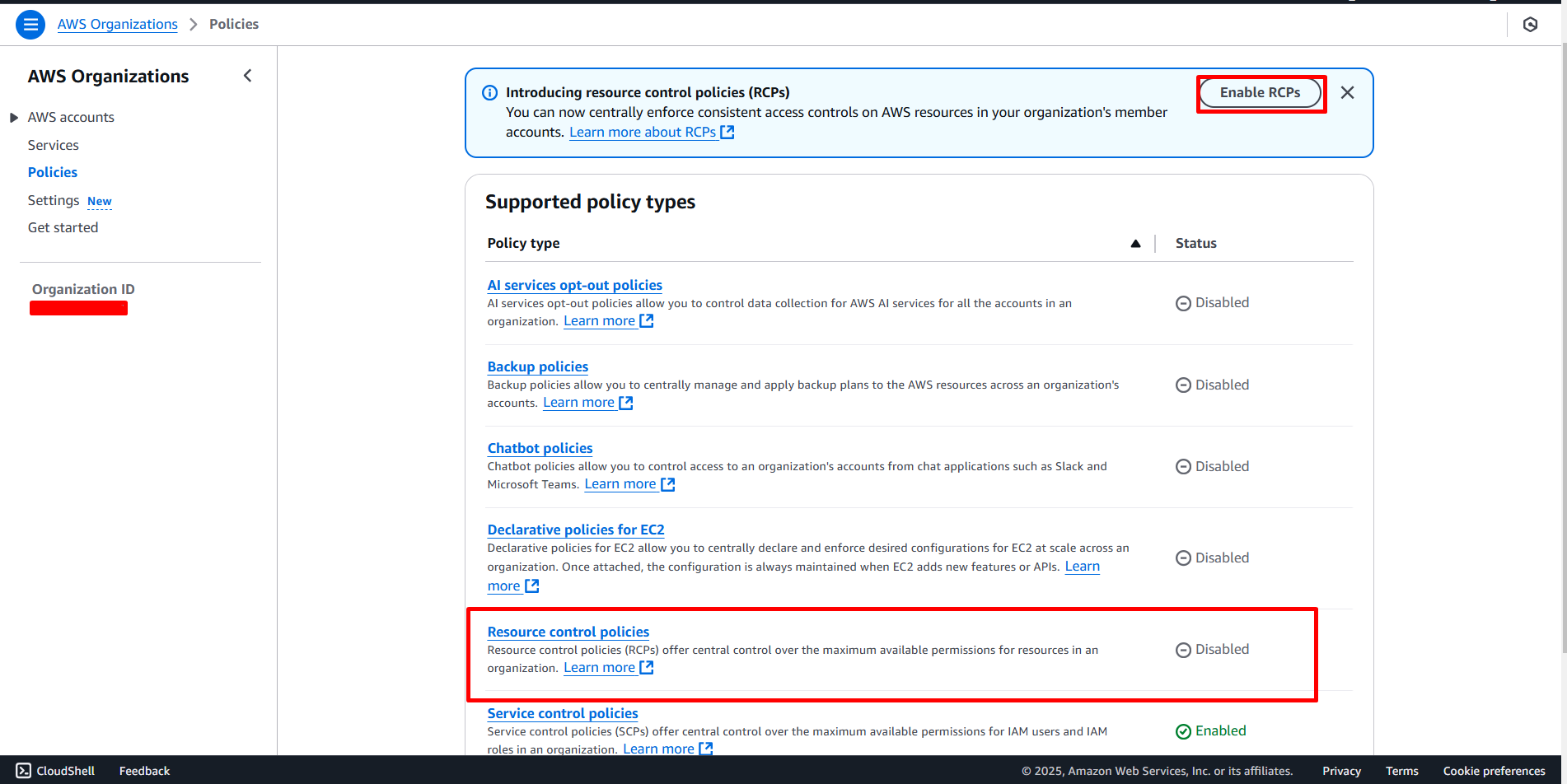
After enabling RCPs, you’ll find a new AWS-managed policy called RCPFullAWSAccess in the Resource control policies page. This policy is automatically created and attached to every entity in your organization—including the root, organizational units (OUs), and AWS accounts.
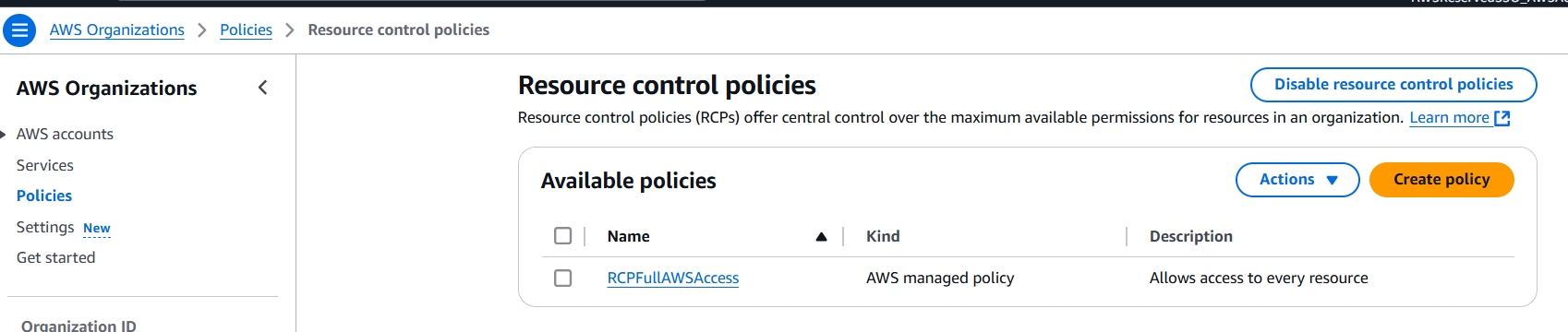
This policy allows all principals to perform any action against the organization’s resources, which means that until you start creating and attaching your own RCPs, all of your existing IAM permissions continue to operate as they did.
This is how it looks:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "*",
"Resource": "*"
}
]
}
Let’s Create Your First RCP
Ready to dive in? Creating your first Resource Control Policy is simpler than you might think. Here’s what you need to know.
Think of RCPs as your organization’s security guard - by default, AWS resources are pretty strict about who gets in. While your developers can set their own access rules, RCPs help your IT team keep everything secure. It’s like having a master key that ensures everyone follows the house rules, even if someone tries to leave the door wide open.
Let’s start with something practical: we’ll create an RCP that makes sure only people within your organization can access your S3 buckets. This is a great way to keep your data safe and secure.
To get started, head over to the Resources control policies page and click Create policy. This will open up the policy editor where you can start building your security rules.
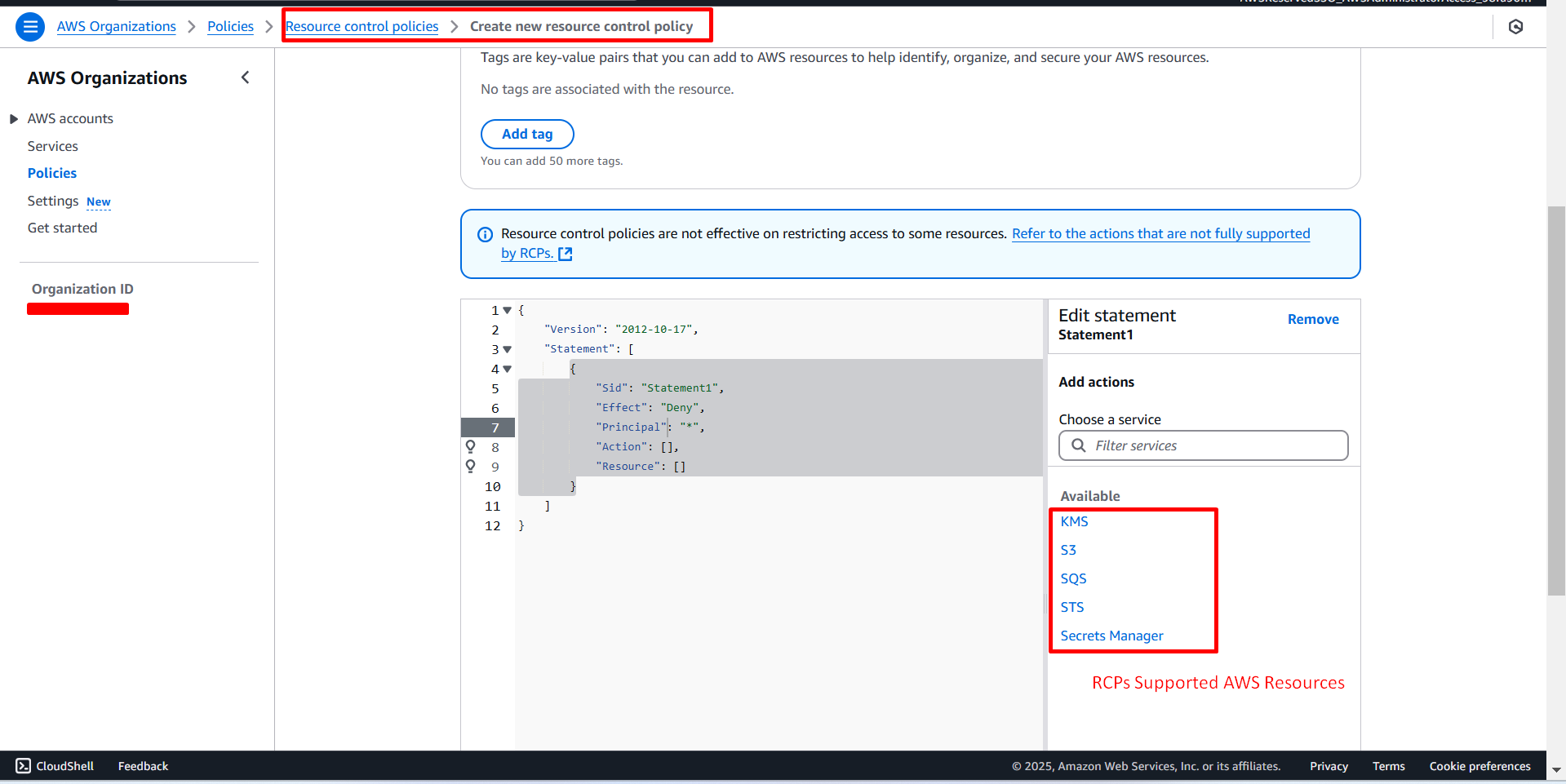
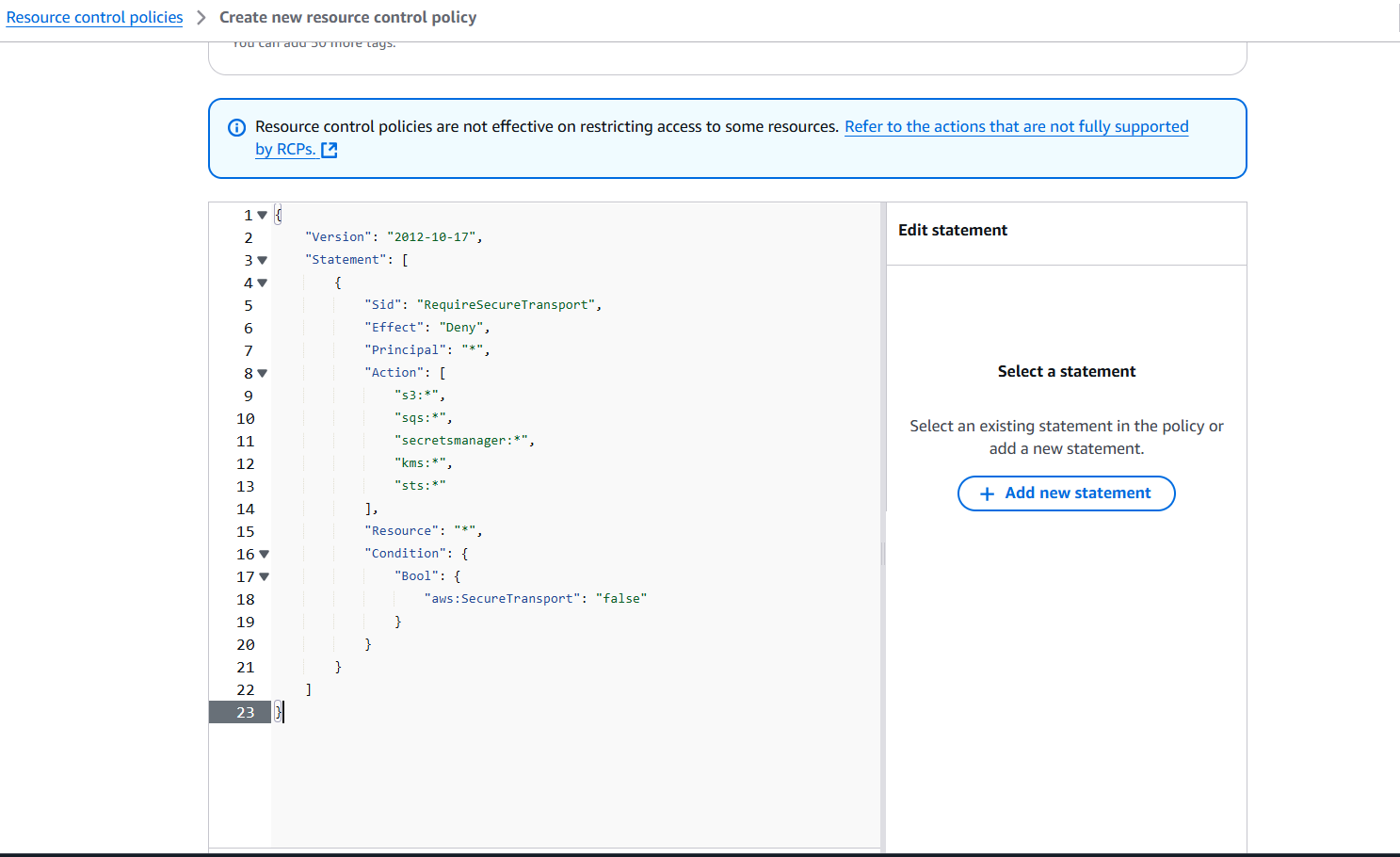
Now, I am going to create RCP policy that ensures all access to your AWS resources happens only through secure HTTPS (TLS) connections. This policy helps prevent potential security risks from unencrypted communications.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "RequireSecureTransport",
"Effect": "Deny",
"Principal": "*",
"Action": [
"s3:*",
"sqs:*",
"secretsmanager:*",
"kms:*",
"sts:*"
],
"Resource": "*",
"Condition": {
"Bool": {
"aws:SecureTransport": "false"
}
}
}
]
}
Let’s break down this Resource Control Policy (RCP) and its components:
Basic Structure
- This is a resource-level policy that works as a guardrail for AWS organizations
- It doesn’t grant permissions directly but sets maximum allowable actions
Policy Elements
"Version": "2012-10-17"- Standard AWS policy version identifier"Effect": "Deny"- Explicitly blocks actions when conditions are met"Principal": "*"- Applies to all principals trying to access the resources"Action": Lists all services this policy controls (S3, SQS, Secrets Manager, KMS, STS)"Condition": Usesaws:SecureTransportto enforce HTTPS connections
Important Characteristics
- Only affects member accounts, not the management account
- Works alongside existing IAM policies
- Applies only to specific AWS services
This specific example serves as a security measure to enforce HTTPS-only access, preventing any unencrypted communications with supported AWS services
Attaching an RCP
You can attach an RCP in the same way as an SCP either to your organization’s root, to an organizational unit (OU), or to individual AWS accounts within your organization.
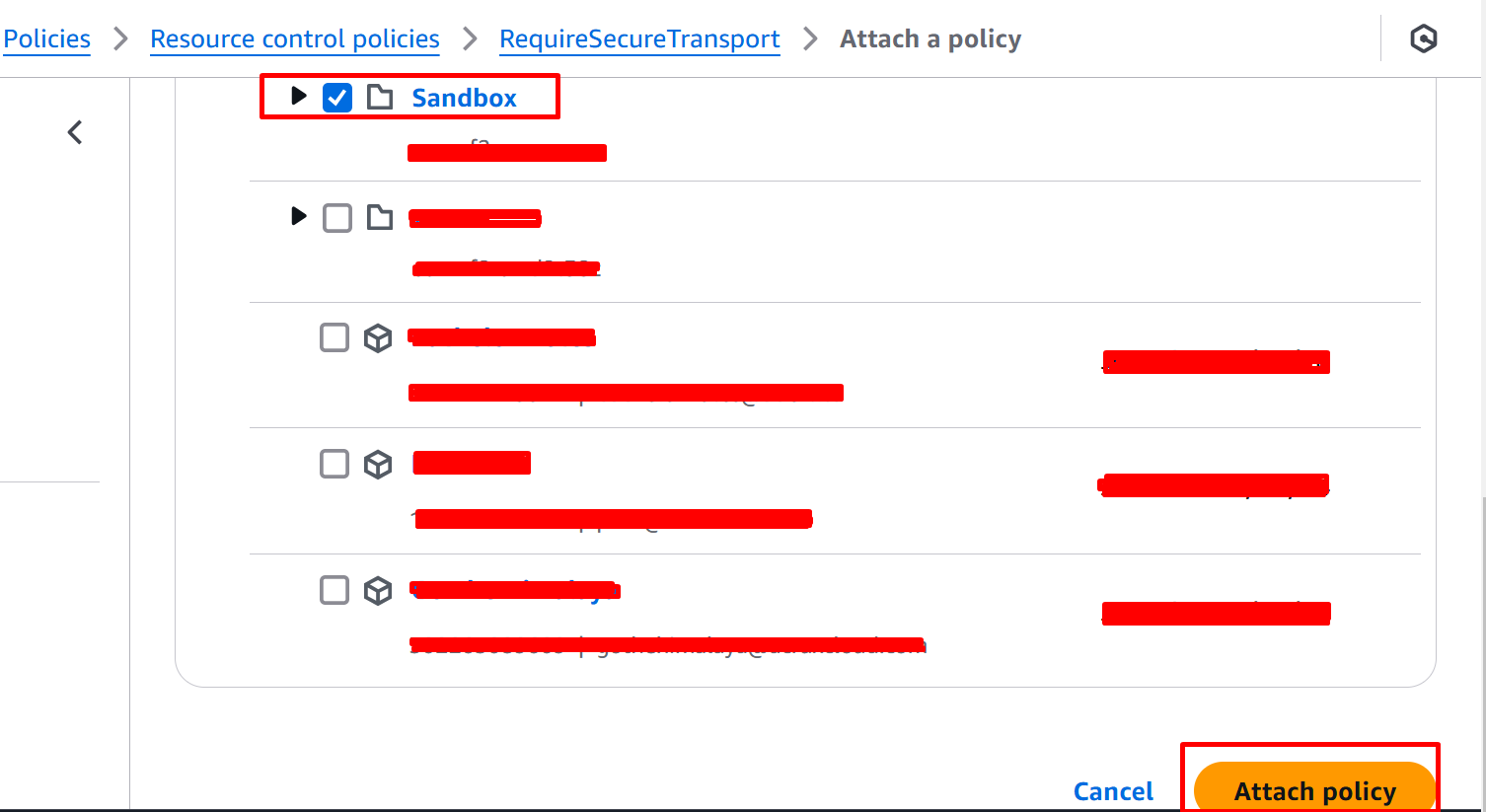
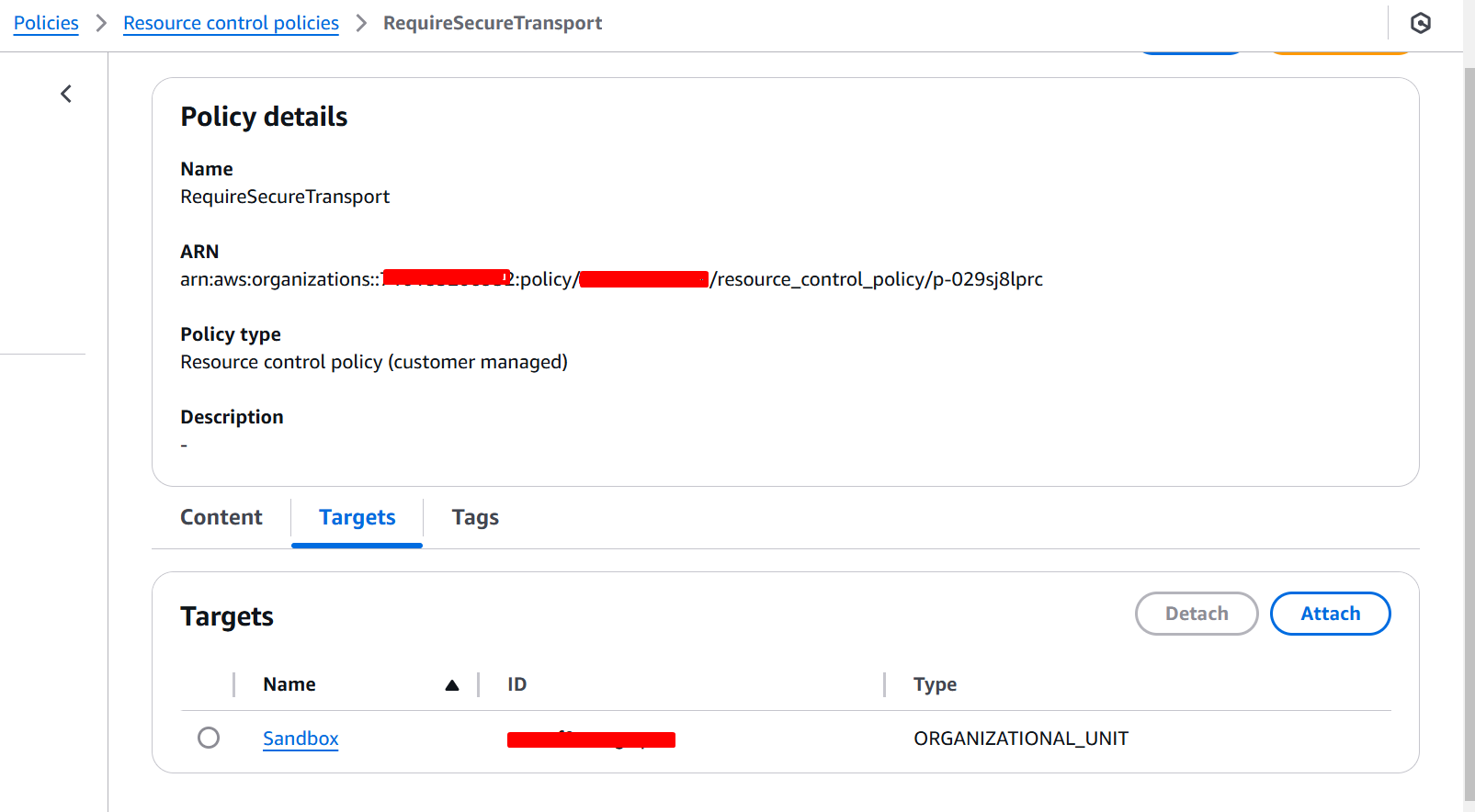
RCP Evaluation
RCPs can be attached at multiple organizational levels, affecting how permissions are evaluated.
Strategy for using RCPs
The default RCPFullAWSAccess policy applies to all levels and maintains normal IAM permissions until custom RCPs are added.
- Use
Denystatements for access restrictions. If any RCP in the hierarchy has a deny statement, that permission is denied. Denystatements can restrict access throughout your organization, such as blocking external access at the root level. Always test before applying root-level RCPs. See Testing effects of RCPs.- A Production OU’s RCP with a
Denystatement affects all accounts below it, blocking service access for Account A and Account B.
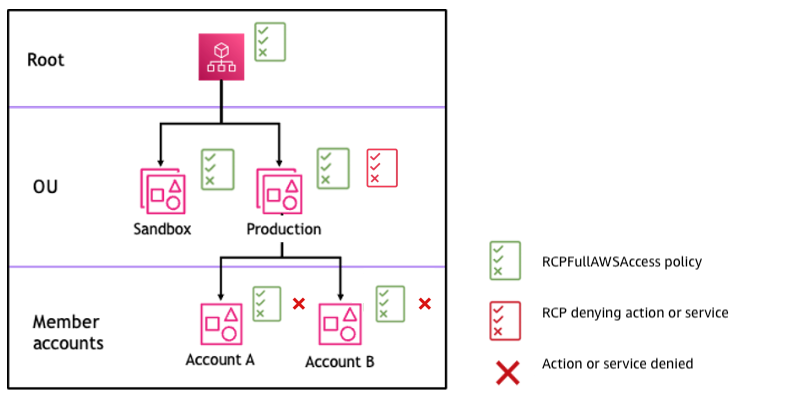
Example organization structure with an Deny statement attached at Production OU and its impact on Account A and Account B
RCP vs SCP Comparison
| Feature | Resource Control Policy (RCP) | Service Control Policy (SCP) |
|---|---|---|
| Primary Purpose | Controls permissions for resources within accounts | Controls permissions for IAM users and roles |
| Scope of Control | Resource-level permissions | Account-level permissions |
| Management Account | Does not affect management account | Does not affect management account |
| Service Coverage | Limited to specific AWS services | Applies to all AWS services |
| Permission Type | Maximum available permissions for resources | Maximum available permissions for principals |
| Policy Evaluation | Evaluated during resource access | Evaluated during API request |
| Service-Linked Roles | Does not affect service-linked roles | Does affect service-linked roles |
| Implementation Level | Organization, OU, or account level | Organization, OU, or account level |
Limitations of AWS RCPs
- 🚫 Limited Service Support: RCPs only work with specific AWS services (S3, STS, KMS, SQS, Secrets Manager)
- 🚫 No Management Account Control: Cannot restrict or control actions in the management account
- 🚫 Service-Linked Role Exemption: RCPs do not affect service-linked roles' permissions
- 🚫 AWS Managed Keys Exclusion: No impact on AWS managed KMS keys
- 🚫 Organization Requirement: Only available in organizations with all features enabled
- 🚫 No Direct Permissions: RCPs cannot grant permissions, they can only restrict them
- 🚫 Policy Size Limit: Subject to AWS policy size limitations (maximum of 5,120 characters)
- 🚫 No Cross-Account Resource Sharing Control: Cannot manage permissions for resources shared across accounts using AWS RAM
Conclusion
RCPs represent a crucial component in AWS’s organizational security toolkit. When properly implemented, they provide an additional layer of security and control over your AWS resources, helping ensure compliance with your organization’s security policies.
Remember to maintain a balance between security and functionality when implementing RCPs, and always follow AWS’s recommended testing procedures before full deployment.
Stay tuned for more. Let’s connect on Linkedin and explore my GitHub for future insights.